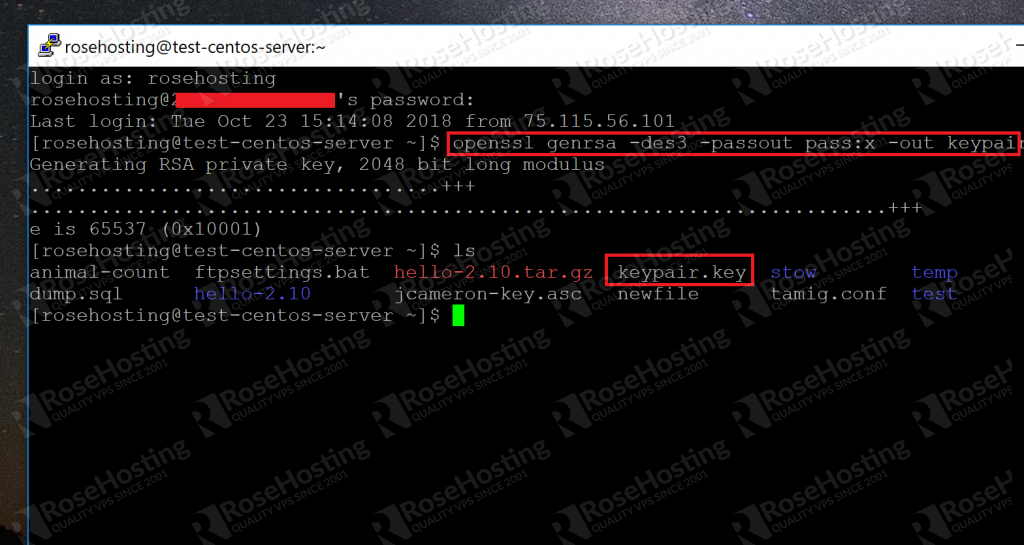
Openssl Generate Rsa 256 Key
Ways to generate symmetric and asymmetric keys. Ask Question. Openssl rsa -in keyfile.key -pubout -out keyfile.pub Now when I read OpenSSL help regarding rsa it says. To generate such a key, use OpenSSL as: openssl rand 16 myaes.key AES-256 expects a key of 256 bit, 32 byte.
Generating a private key can be done in a variety of different ways depending on the type of key, algorithm, bits, and other options your specific use case may require. In this example, we are generating a private key using RSA and a key size of 2048 bits. $ openssl genpkey -algorithm RSA -pkeyopt rsakeygenbits:2048 -out private-key.pem. Apr 28, 2012 Simple Public Key Encryption with RSA and OpenSSL. Apr 28, 2012. Here we’re using the RSAgeneratekey function to generate an RSA public and private key which is stored in an RSA struct. The key length is the first parameter; in this case, a pretty secure 2048 bit key (don’t go lower than 1024, or 4096 for the paranoid), and the public. OpenSSL AES 256-bit Key Management. Ask Question Asked 6 years, 9 months ago. To generate a 256-bit key, a cryptographic module could use a source of entropy to generate random bits, or it could accept a pass phrase and use an extra computational step to derive the 256-bit key from a pass phrase or other input. Why is OpenSSL generated. Hi experts, Please help me to create AES 128 encrypted openssl certificate which can be used for Apache SSL configuration. I am able to create RSA/DSA keys with AES128 encryption using following command. # openssl genrsa -aes128 -out key.pem Is it possible to create AES 128 encrypted key without.
Encrypt and decrypt files to public keys via the OpenSSL Command Line
Published: 25-10-2018 Author: Remy van Elst Text only version of this article
Table of Contents
Openssl Rsa Public Key
This small tutorial will show you how to use the openssl command line to encryptand decrypt a file using a public key. We will first generate a random key,encrypt that random key against the public key of the other person and use thatrandom key to encrypt the actual file with using symmetric encryption.
Because of how the RSA algorithm works it is not possible to encrypt largefiles. If you create a key of n bits, then the file you want to encrypt mustnot larger than (n minus 11) bits. The most effective use of RSA crypto is toencrypt a random generated password, then encrypt the file with the passwordusing symmetric crypto. If the file is larger then the key size the encryptioncommand will fail:
We generate a random file and use that as the key to encrypt the large file withsymmetric crypto. That random file acts as the password so to say. We encryptthe large file with the small password file as password. Then we send theencrypted file and the encrypted key to the other party and then can decrypt thekey with their public key, the use that key to decrypt the large file.
The following commands are relevant when you work with RSA keys:
openssl genrsa: Generates an RSA private keys.openssl rsa: Manage RSA private keys (includes generating a public key from it).openssl rsautl: Encrypt and decrypt files with RSA keys.
The key is just a string of random bytes. We use a base64 encoded string of 128bytes, which is 175 characters. Since 175 characters is 1400 bits, even a smallRSA key will be able to encrypt it.
Get the public key
Let the other party send you a certificate or their public key. If they send toa certificate you can extract the public key using this command:
Generate the random password file
Use the following command to generate the random key:
Office 2019 key generator reddit online. 4. Search on google: dl linux iso site:reddit.com/r/piracy. General queries allowed. Redundant questions that have been previously answered will be removed.
Do this every time you encrypt a file. Use a new key every time!
Update 25-10-2018
The key format is HEX because the base64 format adds newlines. The -passargument later on only takes the first line of the file, so the full key is notused. (Thanks Ken Larson for pointing this to me)
Encrypt the file with the random key
Use the following command to encrypt the large file with the random key:
The file size doesn't grows that much:
It's encrypted however:
Encrypt the random key with the public keyfile
Use the following command to encrypt the random keyfile with the other personspublic key:
You can safely send the key.bin.enc and the largefile.pdf.enc to the otherparty.
You might want to sign the two files with your public key as well.
Decrypt the random key with our private key file
If you want to decrypt a file encrypted with this setup, use the followingcommand with your privte key (beloning to the pubkey the random key was cryptedto) to decrypt the random key:
This will result in the decrypted random key we encrypted the file in.
Decrypt the large file with the random key
Once you have the random key, you can decrypt the encrypted file with thedecrypted key:
This will result in the decrypted large file.
Tags: ca, certificate, decrypt, encrypt, openssl, pki, ssl, tls, tutorialsOpenssl Generate Key File
| # Generate Private Key and Certificate using RSA 256 encryption (4096-bit key) |
| openssl req -x509 -newkey rsa:4096 -keyout privatekey.pem -out certificate.pem -days 365 |
| # Alternatively, setting the '-newkey' parameter to 'rsa:2048' will generate a 2048-bit key. |
| # Generate PKCS#12 (P12) file for cert; combines both key and certificate together |
| openssl pkcs12 -export -inkey privatekey.pem -in certificate.pem -out cert.pfx |
| # Generate SHA256 Fingerprint for Certificate and export to a file |
| openssl x509 -noout -fingerprint -sha256 -inform pem -in certificate.pem >> fingerprint.txt |
| # Generate SHA1 Fingerprint for Certificate and export to a file |
| #openssl x509 -noout -fingerprint -sha1 -inform pem -in certificate.pem >> fingerprint.txt |
| # FYI, it's best practice to use SHA256 instead of SHA1 for better security, but this shows how to do it if you REALLY need to. |
commented Nov 7, 2019
Here's a couple useful links related to this: Monster hunter generations ultimate main key quests online. |