Openssl Generate Self Signed Certificate With Private Key
- Self Signed Certificate Windows
- Self Signed Certificate Iis
- Openssl Create Self Signed Certificate With Private Key
- Openssl Self Signed Certificate Linux
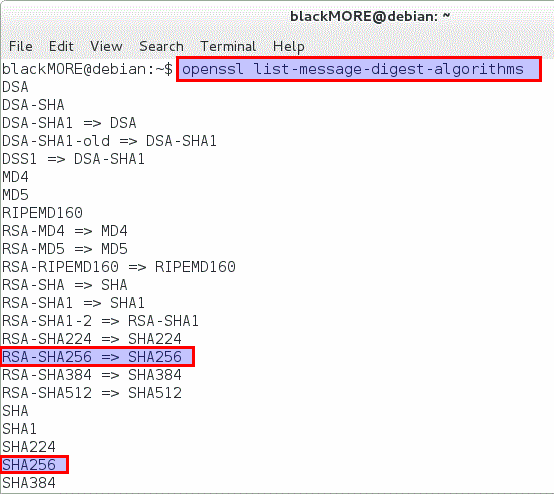
Mar 24, 2015 Online Service. Cert-Depot - It can create certificates in both unencrypted PEM format, and PFX. Install openssl package for your operating system from here; Generating a private key: openssl genrsa 2048 private.pem Generating the self signed certificate: openssl req -x509 -new -key private.pem -out public.pem If required, creating PFX: openssl pkcs12 -export -in public.pem -inkey. You upload the digital certificate to the custom connected app that is also required for JWT-based authorization. You can use your own private key and certificate issued by a certification authority. Alternatively, you can use OpenSSL to create a key and a self-signed digital certificate. Generate certificate signing request (CSR) with the key. Using the private key generated in the previous step, we need to create a certificate signing request. You can generate the certificate signing request with an interactive prompt or by providing the extra certificate information in the command line arguments. Apr 12, 2020 Create self signed certificate in Red Hat Linux. Create self signed certificate CentOS 7. CentOS trust self signed certificate. Install SSL certificate Red Hat 7. Create self signed certificate Red Hat Linux or CentOS 7. Openssl generate self signed certificate sha256 CentOS.
-->The Application Gateway v2 SKU introduces the use of Trusted Root Certificates to allow backend servers. This removes authentication certificates that were required in the v1 SKU. The root certificate is a Base-64 encoded X.509(.CER) format root certificate from the backend certificate server. It identifies the root certificate authority (CA) that issued the server certificate and the server certificate is then used for the TLS/SSL communication.
Application Gateway trusts your website's certificate by default if it's signed by a well-known CA (for example, GoDaddy or DigiCert). You don't need to explicitly upload the root certificate in that case. For more information, see Overview of TLS termination and end to end TLS with Application Gateway. However, if you have a dev/test environment and don't want to purchase a verified CA signed certificate, you can create your own custom CA and create a self-signed certificate with it.
Note
Self-signed certificates are not trusted by default and they can be difficult to maintain. Also, they may use outdated hash and cipher suites that may not be strong. For better security, purchase a certificate signed by a well-known certificate authority.
In this article, you will learn how to:
- Create your own custom Certificate Authority
- Create a self-signed certificate signed by your custom CA
- Upload a self-signed root certificate to an Application Gateway to authenticate the backend server
Prerequisites
OpenSSL on a computer running Windows or Linux
While there could be other tools available for certificate management, this tutorial uses OpenSSL. You can find OpenSSL bundled with many Linux distributions, such as Ubuntu.
A web server
For example, Apache, IIS, or NGINX to test the certificates.
An Application Gateway v2 SKU
If you don't have an existing application gateway, see Quickstart: Direct web traffic with Azure Application Gateway - Azure portal.
Create a root CA certificate
Create your root CA certificate using OpenSSL.
Create the root key
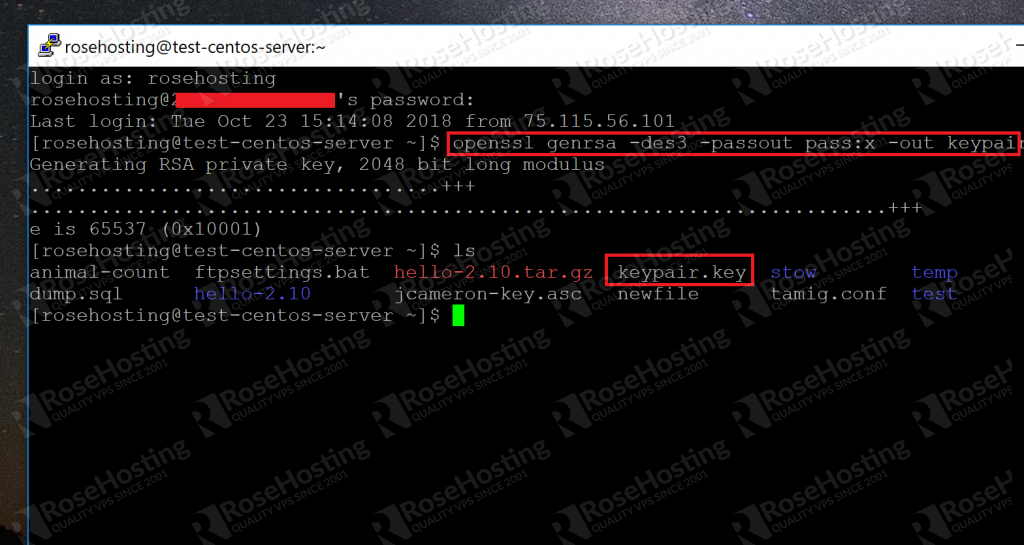
Sign in to your computer where OpenSSL is installed and run the following command. This creates a password protected key.
At the prompt, type a strong password. For example, at least nine characters, using upper case, lower case, numbers, and symbols.
Create a Root Certificate and self-sign it
Use the following commands to generate the csr and the certificate.
The previous commands create the root certificate. You'll use this to sign your server certificate.
When prompted, type the password for the root key, and the organizational information for the custom CA such as Country, State, Org, OU, and the fully qualified domain name (this is the domain of the issuer).
Create a server certificate
Next, you'll create a server certificate using OpenSSL.
Create the certificate's key
Use the following command to generate the key for the server certificate.
Create the CSR (Certificate Signing Request)
The CSR is a public key that is given to a CA when requesting a certificate. The CA issues the certificate for this specific request. Os x generate public ssh keys.
Online CSR and Key Generator SSL.com’s public CSR and Key Generator is currently down for maintenance as part of our website’s redesign and update. An Online RSA Public and Private Key Generator. Sep 6 th, 2013. I was recently in a meeting where a person needed to generate a private and public key for RSA encryption, but they were using a PC (Windows). This is something that is easily done via a terminal using ssh-keygen on Mac and Linux. Online RSA Key Generator. Key Size 1024 bit. 512 bit; 1024 bit; 2048 bit; 4096 bit Generate New Keys Async. RSA Encryption Test. Text to encrypt: Encrypt / Decrypt. Generate online private and public key for ssh, putty, github, bitbucket Save both of keys on your computer (text file, dropbox, evernote etc)!!! The generated keys are RANDOM and CAN'T be restored. You can create keys without creating an account. Usage Guide - RSA Encryption and Decryption Online. In the first section of this tool, you can generate public or private keys. To do so, select the RSA key size among 515, 1024, 2048 and 4096 bit. 
Note
The CN (Common Name) for the server certificate must be different from the issuer's domain. For example, in this case, the CN for the issuer is www.contoso.com and the server certificate's CN is www.fabrikam.com.
Use the following command to generate the CSR:
When prompted, type the password for the root key, and the organizational information for the custom CA: Country, State, Org, OU, and the fully qualified domain name. This is the domain of the website and it should be different from the issuer.
Generate the certificate with the CSR and the key and sign it with the CA's root key
Use the following command to create the certificate:
Verify the newly created certificate
Use the following command to print the output of the CRT file and verify its content:
Verify the files in your directory, and ensure you have the following files:
- contoso.crt
- contoso.key
- fabrikam.crt
- fabrikam.key
Self Signed Certificate Windows
Configure the certificate in your web server's TLS settings
In your web server, configure TLS using the fabrikam.crt and fabrikam.key files. If your web server can't take two files, you can combine them to a single .pem or .pfx file using OpenSSL commands.
IIS
For instructions on how to import certificate and upload them as server certificate on IIS, see HOW TO: Install Imported Certificates on a Web Server in Windows Server 2003.
For TLS binding instructions, see How to Set Up SSL on IIS 7.
Apache
The following configuration is an example virtual host configured for SSL in Apache:
NGINX
The following configuration is an example NGINX server block with TLS configuration:
Access the server to verify the configuration
Add the root certificate to your machine's trusted root store. When you access the website, ensure the entire certificate chain is seen in the browser.
Note
It's assumed that DNS has been configured to point the web server name (in this example, www.fabrikam.com) to your web server's IP address. If not, you can edit the hosts file to resolve the name.
Browse to your website, and click the lock icon on your browser's address box to verify the site and certificate information.
Verify the configuration with OpenSSL
Or, you can use OpenSSL to verify the certificate.
Upload the root certificate to Application Gateway's HTTP Settings
To upload the certificate in Application Gateway, you must export the .crt certificate into a .cer format Base-64 encoded. Since .crt already contains the public key in the base-64 encoded format, just rename the file extension from .crt to .cer.
Azure portal
To upload the trusted root certificate from the portal, select the HTTP Settings and choose the HTTPS protocol.
Self Signed Certificate Iis
Azure PowerShell
Or, you can use Azure CLI or Azure PowerShell to upload the root certificate. The following code is an Azure PowerShell sample.
Note
The following sample adds a trusted root certificate to the application gateway, creates a new HTTP setting and adds a new rule, assuming the backend pool and the listener exist already.
Verify the application gateway backend health
Openssl Create Self Signed Certificate With Private Key
- Click the Backend Health view of your application gateway to check if the probe is healthy.
- You should see that the Status is Healthy for the HTTPS probe.
Next steps
To learn more about SSLTLS in Application Gateway, see Overview of TLS termination and end to end TLS with Application Gateway.
Openssl Self Signed Certificate Linux
| # Define where to store the generated certs and metadata. |
| DIR='$(pwd)/tls' |
| # Optional: Ensure the target directory exists and is empty. |
| rm -rf '${DIR}' |
| mkdir -p '${DIR}' |
| # Create the openssl configuration file. This is used for both generating |
| # the certificate as well as for specifying the extensions. It aims in favor |
| # of automation, so the DN is encoding and not prompted. |
| cat >'${DIR}/openssl.cnf'<<EOF |
| [req] |
| default_bits = 2048 |
| encrypt_key = no # Change to encrypt the private key using des3 or similar |
| default_md = sha256 |
| prompt = no |
| utf8 = yes |
| # Speify the DN here so we aren't prompted (along with prompt = no above). |
| distinguished_name = req_distinguished_name |
| # Extensions for SAN IP and SAN DNS |
| req_extensions = v3_req |
| # Be sure to update the subject to match your organization. |
| [req_distinguished_name] |
| C = US |
| ST = California |
| L = The Cloud |
| O = Demo |
| CN = My Certificate |
| # Allow client and server auth. You may want to only allow server auth. |
| # Link to SAN names. |
| [v3_req] |
| basicConstraints = CA:FALSE |
| subjectKeyIdentifier = hash |
| keyUsage = digitalSignature, keyEncipherment |
| extendedKeyUsage = clientAuth, serverAuth |
| subjectAltName = @alt_names |
| # Alternative names are specified as IP.# and DNS.# for IP addresses and |
| # DNS accordingly. |
| [alt_names] |
| IP.1 = 1.2.3.4 |
| DNS.1 = my.dns.name |
| EOF |
| # Create the certificate authority (CA). This will be a self-signed CA, and this |
| # command generates both the private key and the certificate. You may want to |
| # adjust the number of bits (4096 is a bit more secure, but not supported in all |
| # places at the time of this publication). |
| # |
| # To put a password on the key, remove the -nodes option. |
| # |
| # Be sure to update the subject to match your organization. |
| openssl req |
| -new |
| -newkey rsa:2048 |
| -days 120 |
| -nodes |
| -x509 |
| -subj '/C=US/ST=California/L=The Cloud/O=My Company CA' |
| -keyout '${DIR}/ca.key' |
| -out '${DIR}/ca.crt' |
| # |
| # For each server/service you want to secure with your CA, repeat the |
| # following steps: |
| # |
| # Generate the private key for the service. Again, you may want to increase |
| # the bits to 4096. |
| openssl genrsa -out '${DIR}/my-service.key' 2048 |
| # Generate a CSR using the configuration and the key just generated. We will |
| # give this CSR to our CA to sign. |
| openssl req |
| -new -key '${DIR}/my-service.key' |
| -out '${DIR}/my-service.csr' |
| -config '${DIR}/openssl.cnf' |
| # Sign the CSR with our CA. This will generate a new certificate that is signed |
| # by our CA. |
| openssl x509 |
| -req |
| -days 120 |
| -in '${DIR}/my-service.csr' |
| -CA '${DIR}/ca.crt' |
| -CAkey '${DIR}/ca.key' |
| -CAcreateserial |
| -extensions v3_req |
| -extfile '${DIR}/openssl.cnf' |
| -out '${DIR}/my-service.crt' |
| # (Optional) Verify the certificate. |
| openssl x509 -in '${DIR}/my-service.crt' -noout -text |
| # Here is a sample response (truncate): |
| # |
| # Certificate: |
| # Signature Algorithm: sha256WithRSAEncryption |
| # Issuer: C = US, ST = California, L = The Cloud, O = My Organization CA |
| # Subject: C = US, ST = California, L = The Cloud, O = Demo, CN = My Certificate |
| # # .. |
| # X509v3 extensions: |
| # X509v3 Basic Constraints: |
| # CA:FALSE |
| # X509v3 Subject Key Identifier: |
| # 36:7E:F0:3D:93:C6:ED:02:22:A9:3D:FF:18:B6:63:5F:20:52:6E:2E |
| # X509v3 Key Usage: |
| # Digital Signature, Key Encipherment |
| # X509v3 Extended Key Usage: |
| # TLS Web Client Authentication, TLS Web Server Authentication |
| # X509v3 Subject Alternative Name: |
| # IP Address:1.2.3.4, DNS:my.dns.name |
| # |