Wpa Pre Shared Key Generator
- Setup Wpa Pre Shared Key Linksys
- Wpa Pre Shared Key Vizio
- Wpa Pre Shared Key Generator For Sale
- Wpa2 Pre Shared Key Generator
Pre-shared keys (PSK) are the most common authentication method for site-to-site IPsec VPN tunnels. So what’s to say about the security of PSKs? What is its role for the network security? How complex should PSKs be? Should they be stored additionally? What happens if an attacker catches my PSKs?
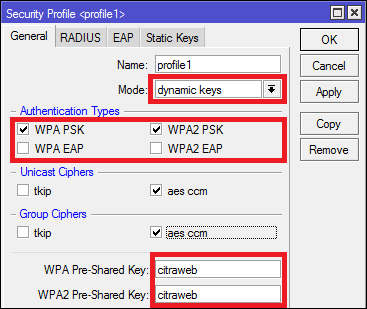
Password Generator: 2,645 sets of passwords generated per day. So the entire 64 characters is equivalent to 256 binary bits — which is the actual binary key length used by the WiFi WPA pre-shared key (PSK). Some WPA-PSK user interfaces (such as the one in Windows XP) allows the 256-bit WPA pre-shared key to be directly provided as 64. Or you can use serial numbers, MAC addresses, or you could call each other and exchange two colours, favourite sports teams, etc. Note that whatever one party enters as 'Key 1' the other party must enter as 'Key 1', and whatever one party enters as 'Key 2' the other party must also enter as 'Key 2'. TJdME1o32Cl&zcHw/Pf%nSYigtOVF-uvUr4GbDh!8 #B65pa,K+qRZWLy90xAjI. Download keys Generate a new encryption keys. Read: Security & Insecurity in pre-shared key mode. Sharing beautiful knowledge of the world. This WPA-PSK calculator provides an easy way to convert a SSID and WPA Passphrase to the 256-bit pre-shared ('raw') key used for key derivation.
Setup Wpa Pre Shared Key Linksys
I am listing my best practice steps for generating PSKs.
Pre-Shared Keys in IPsec
The following section is related to site-to-site VPNs only and NOT to remote access VPNs.
- The pre-shared key is merely used for authentication, not for encryption! IPsec tunnels rely on the ISAKMP/IKE protocols to exchange the keys for encryption, etc. But before IKE can work, both peers need to authenticate each other (mutual authentication). This is the only part in which the PSKs are used (RFC 2409).
- If static IP addresses are used on both sides (= main mode can be used), an attacker who has the PSK must also spoof/redirect these public addresses over himself in order to establish a VPN connection. That is: Even if an attacker has a PSK, he must spoof a public IP address to use it to authenticate against the other side. This is quite unrealistic for normal persons with common ISP connections. Even skilled hackers must be able to inject falsified BGP routes or to sit nearby the customers default gateway/router.
- But: If one remote side has only a dynamic IP address, IKE must use the aggressive mode for its authentication. In this scenario, a hash from the PSK traverses the Internet. An attacker can do an offline brute-force attack against this hash. That is: If the PSK is not complex enough, the attacker could succeed and would be able to establish a VPN connection to the network (if he furthermore knows the IDs of the site-to-site VPN peers which is no problem since they traverse through the Internet in plaintext, too).
Best Practice for PSKs
Since the PSKs must be configured on each side only once, it should be no problem to write 20-40 letters on the firewall. Thereby, a really complex key can be generated and used for the authentication of the VPN peer. Here are my tips:
Wpa Pre Shared Key Vizio
- Generate a new/different PSK for every VPN tunnel.
- Use a password/passphrase generator for the creation of the PSK.
- Generate a long PSK with at least 30 chars, to resist a brute-force attack. (See my article about password complexity.) To avoid problems, use only alphanumeric chars. Since the PSK with 30 chars is really long, the “small” character set of only 62 alphabets and numerals is no problem. The security level in this example would be round about 178 bit (since ).
- Do NOT send the PSK to your peer over the Internet, but via phone, fax, or SMS.
- There is no need to store the PSK anywhere else. If it is configured on both sides, you can discard it. In the worst case, you need to generate and transfer a new one.
Further Reading
- RFC 2409: The Internet Key Exchange (IKE)
- RFC 4301: Security Architecture for the Internet Protocol
- Michael Thumann, Enno Rey: PSK Cracking using IKE Aggressive Mode [PDF]
- eTutorials: Attacking IPsec VPNs
Featured image: “Scrabble” by Wasili is licensed under CC BY-NC-ND 2.0.
IFM supplies network engineering services for $NZ180+GST per hour. Call of duty ghosts serial key generator pc. If you require assistance with designing or engineering a Cisco network - hire us!

Wpa Pre Shared Key Generator For Sale
Note: This page uses client side Javascript. It does not transmit any information entered to IFM.
You are building a site to site VPN and need to exchange the PSK. However you are not allowed to email it, and TXTing never works as it mangles the PSK. What to do?
This tool uses client side javascript - so no information is ever transmitted - and generates a random PSK in your own web browser that rolls every 24 hours. All it requires is for both parties to have their machine clocks approximately correctly (so both machines calculate the same PSK).
Optionally, to make a more variable key, you can enter two encoding keys, and these keys must be exchanged between both parties. For example, you can make the two keys the public IP address of the two VPN terminators. Or you can use serial numbers, MAC addresses, or you could call each other and exchange two colours, favourite sports teams, etc. Note that whatever one party enters as 'Key 1' the other party must enter as 'Key 1', and whatever one party enters as 'Key 2' the other party must also enter as 'Key 2'.
Wpa2 Pre Shared Key Generator
Then the tool will take your two keys, add a unique salt for that 24 hour period, and generate a nasty PSK that no person would ever guess - and that has never been transmitted over any medium, ever.
This page uses Javascript, and alas, your browser does not support it.