Windows Generate Private Key And Csr
Generate CSR - OpenSSL
Introduction
If the device on which you are generating the CSR is also the (only) device the certificate will be used, you should leave “make private key exportable” unchecked. This will prevent the certificate from being exported from the machine in an easy fashion. (It can still be sniffed from memory by an advanced attacker who has compromised the box).
Jun 04, 2017 Depending on how you generate your certificate you might need to use the private key that IIS used to create this CSR. Here’s how to extract it: Open Microsoft Management Console by typing mmc on. Sep 09, 2019 This document describes the procedure to generate certificates which have to be uploaded with every fresh installation of AMP Virtual Private Cloud (VPC). With the introduction of AMP Private Cloud 3.X, hostnames and certificate/key pairs are.
This article provides step-by-step instructions for generating a Certificate Signing Request (CSR) in OpenSSL. This is most commonly required for web servers such as Apache HTTP Server and NGINX. If this is not the solution you are looking for, please search for your solution in the search bar above.
Switch to a working directory
Windows Generate Private Key And Csr
GNU/Linux & Mac OS X users:
Open a terminal and browse to a folder where you would like to generate your keypair
Windows Users:
Navigate to your OpenSSL 'bin' directory and open a command prompt in the same location.
Generate a CSR & Private Key:
openssl req -out CSR.csr -new -newkey rsa:2048 -keyout privatekey.key
To generate a 4096-bit CSR you can replace the rsa:2048 syntax with rsa:4096 as shown below.
openssl req -out CSR.csr -new -newkey rsa:4096 -keyout privatekey.key
Note: You will be prompted to enter a password in order to proceed. Keep this password as you will need it to use the Certificate.
Fill out the following fields as prompted:
Note: The following characters can not be accepted: < > ~ ! @ # $ % ^ * / ( ) ?.,&
| Field | Example |
|---|---|
| Country Name | US (2 Letter Code) |
| State or Province | New Hampshire (Full State Name) |
| Locality | Portsmouth (Full City name) |
| Organization | GMO GlobalSign Inc (Entity's Legal Name) |
| Organizational Unit | Support (Optional, e.g. a department) |
| Common Name | www.globalsign.com (Domain or Entity name) |
You should now have a Private Key (privatekey.key) which should stay on your computer, and a Certificate Signing Request (CSR.csr), which can be submitted to GlobalSign to sign your public key. Each of these files can be viewed in a plain text editor such as Notepad, TextEdit, Vi, Nano, and Notepad++.
Introduction
This document describes the procedure to generate certificates which have to be uploaded with every fresh installation of AMP Virtual Private Cloud (VPC). With the introduction of AMP Private Cloud 3.X, hostnames and certificate/key pairs are required for all of the following services:
- Administration Portal
- Authentication (new in Private Cloud 3.X)
- FireAMP Console
- Disposition Server
- Disposition Server - Extended Protocol
- Disposition Update Service
- Firepower Management Center
Here, we will discuss a quick way to generate and upload the required certificates. You may tweak each of the parameters, including the hashing algorithm, key size, and others, as per your organization's policy, and your mechanism of generating these certificates might not match with what is detailed here.
Prerequisites
Components Used
Cisco recommends that you have knowledge of these topics:
- Windows Server 2008 onwards
- AMP Private Cloud installation
- Public Key Infrastructure
Requirements
The information in this document is based on these software and hardware versions:
- Windows Server 2008
- CentOS 7
- AMP Virtual Private Cloud 3.0.2
Warning: The procedure mentioned below can vary as per your CA server configuration. It is expected that the CA server of your choice is already provisioned and the configuration of the same has been completed. The following technote just describes an example of generating the certificates and Cisco TAC will not be involved in troubleshooting issues related to certificate generation and/or CA server issues of any kind.
Generate Certificates on Window Server
Ensure that the following roles are installed and configured on your Windows Server.
- Active Directory Certificate Services
- Certification Authority
- Certification Authority Web Enrollment
- Online Responder
- Certificate Enrollment Web Service
- Certificate Enrollment Policy Web Service
- Active Directory Domain Services
- DNS Servers
- Web Server (IIS)
Generate a Certificate Signing Request (CSR)
Step 1. Navigate to MMC console, and add the Certificates snap-in for your computer account as shown in the image here.
Step 2. Drill down Certificates (Local Computer) > Personal > Certificates.
Step 3. Right click on the empty space and select All Tasks > Advanced Operations > Create Custom Request
Step 4. Click Next at the Enrollment window.
Step 5. Select your certificate enrollment policy and click Next.
Step 6. Choose the template as Web Server and click Next.
Step 7. If your 'Web Server' template has been configured correctly and is available for enrollment, you will see the status as 'Available' here. Click 'Details' to expand click on Properties.
Step 8. At a minimum, add the CN and DNS attributes. The rest of the attributes can be added as per your security requirements.
Step 9. Optionally, give a Friendly Name under the General tab.
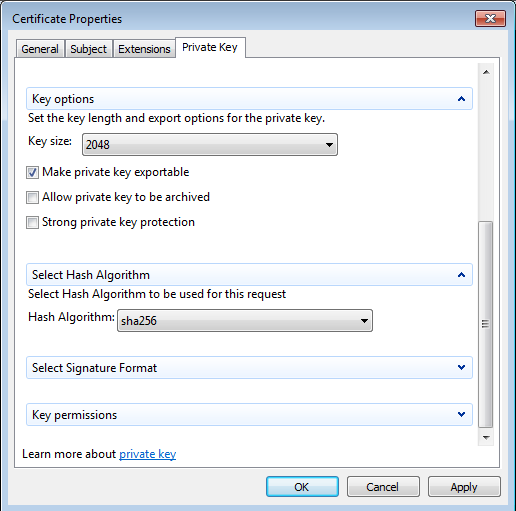
Step 10. Click on the PrivateKey tab and ensure that you're enabling Make private key exportable under the Key Options section.
Step 11. Finally, click on OK. This should lead you to the Certificate Enrollment dialog from where you can click on Next.
Step 12. Browse to a location to save the .req file which will be submitted to the CA server for signing.
Submitting the CSR to the CA and generating the certificate
Step 1. Navigate to your MS AD Certificate Services Web Page as below and click 'Request a Certificate'
Step 2. Click on the advanced certificate request link.
Step 3. Click on Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
Step 4. Open the contents of the previously saved .req file (CSR) via Notepad. Copy the contents and paste it here. Ensure that the Certificate Template is selected as Web Server
Step 5. Finally, click on Submit.
Step 6. At this point, you should be able to Download the certificate as shown in the image here.
Exporting the Private Key and converting to PEM format
Step 1. Install the certificate into your Certificate Store by opening the .cer file and clicking on Install Certificate.
Step 2. Navigate to the MMC snap-in that was selected earlier.
Step 3. Navigate to the store where the certificate was installed.
Step 4. Right click the correct certificate, select All Tasks > Export.
Step 5. At the Certificate Export Wizard, confirm to export the private key as shown in the image.
Step 6. Enter a password and click Next to save the private key on your disk.
Step 7. This will save the private key in .PFX format, however, this needs to be converted to .PEM format to use this with AMP VPC.
Step 8. Install OpenSSL libraries from here:https://wiki.openssl.org/index.php/Binaries
Step 9. Open a command prompt window and change to the directory where you installed OpenSSL.
Step 10. Run the following command to extract the private key and save it to a new file: (If your PFX file is not in the same path as where the OpenSSL library is stored, you will have to specify the exact path along with the filename)
Step 11. Now run the following command to also extract the public cert and save it to a new file:
Generate Certificate on Linux Server
Ensure that the Linux server that you're trying to generate the required certificates has the OpenSSL libraries installed. Verifying if this and the procedure listed below will vary from the Linux distribution that you're running. This portion has been documented, as done on a CentOS 7 server.
Generate Self Signed RootCA
Step 1. Generate the Private Key for Root CA certificate
Step 2. Generate the CA certificate
Generate a certificate for each service
Create the certificate for Authentication, Console, Disposition, Disposition-Extended, Update server, Firepower Management Center(FMC) service as per the DNS name entry. You need to repeat below certificate generate process for each service (Authentication, Console etc.)
Generate Private key
Replace the <example.key> with actual certificate key such as Auth-Cert.key.
Generate CSR
Replace the <example.csr> with actual certificate CSR such as Auth-Cert.csr
Generate Certificate
Replace <example.csr>, <example.crt> with actual certificate CSR and certificate name
Adding The Certificates to AMP VPC
Step 1. Once the certificates are generated from any of the above methods, upload the corresponding certificate for each of the services. If they have been generated correctly, all the check marks are enabled as seen in the image here.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
Generate Key And Csr
There is currently no specific troubleshooting information available for this configuration.
Likewise, if a PDF document is encrypted with a certificate, the user must decrypt the PDF document with the public key that corresponds to the certificate (private key) that was used to encrypt the PDF document. Generate pkcs7 decrypt key acrobat pro free. If a PDF document is encrypted with a password, the user must specify the open password before the document can be viewed in Adobe Reader or Adobe Acrobat.